Caesar Cipher Examples and Practice Problems with Solutions: Complete Practice Guide
Master Caesar cipher with 25+ hands-on practice problems, step-by-step solutions, and programming examples. From basic encryption to advanced frequency analysis and brute force decryption techniques.

Can you crack this Caesar cipher text in 5 minutes? "WKLV LV D WHVW PHVVDJH" - This seemingly random string is actually an English message encrypted using the Caesar cipher substitution method. If you want to challenge your cryptographic skills and learn cipher breaking techniques, systematic practice with Caesar cipher examples is the best way to master this classical encryption algorithm. Before diving into these practice problems, you might want to review our complete beginner's guide to Caesar cipher for fundamental concepts.
On programming platforms like HackerRank and LeetCode, Caesar cipher programming challenges and algorithm practice problems have always been among the most popular cryptography exercises for computer science students and developers. Similarly, in CTF competitions like picoCTF, Caesar cipher serves as an entry-level cryptographic problem that provides thousands of learners with their first taste of successful code-breaking. This widespread application proves the important role of practical exercises in cryptography learning.
This comprehensive guide provides a complete Caesar cipher practice system with over 25 hands-on exercises, covering systematic training from basic manual encryption calculations to advanced cryptanalysis programming implementations and automated decryption techniques. For theoretical background, see our algorithm and mathematical formula guide. Whether you're a beginner just getting into cryptography, a programmer seeking more challenges, or a teacher needing educational materials, you'll find suitable practice content here.
We'll progress from simple to complex in order: manual encryption and decryption exercises, frequency analysis challenges, pattern recognition training, and finally programming implementations and CTF-style comprehensive problems. Each exercise provides detailed solution steps and analytical thinking, ensuring you understand not just the how, but also the why.
The practice problems in this guide are designed to mirror real-world scenarios you might encounter in cybersecurity competitions, academic coursework, or professional cryptographic work. By working through these systematically, you'll develop the analytical thinking skills that form the foundation of all cryptographic analysis.
I remember when I first attempted a Caesar cipher challenge in a college CTF competition - what seemed like gibberish suddenly clicked into readable English after trying the seventh shift value. That "aha!" moment is exactly what these exercises aim to recreate for you. Whether you're a student pulling an all-nighter before a cryptography exam, a developer adding security features to an app, or simply someone who loves puzzles, these hands-on exercises will build your confidence one successful decryption at a time.
Basic Caesar Cipher Practice Exercises
These foundational exercises will teach you the core mechanics of Caesar cipher encryption and decryption. Master these basics before moving to advanced cryptanalysis techniques.
Manual Caesar Cipher Encryption Practice
Hand-calculation skills are essential for understanding how Caesar cipher algorithms work internally. These exercises build your mental model of the encryption process.
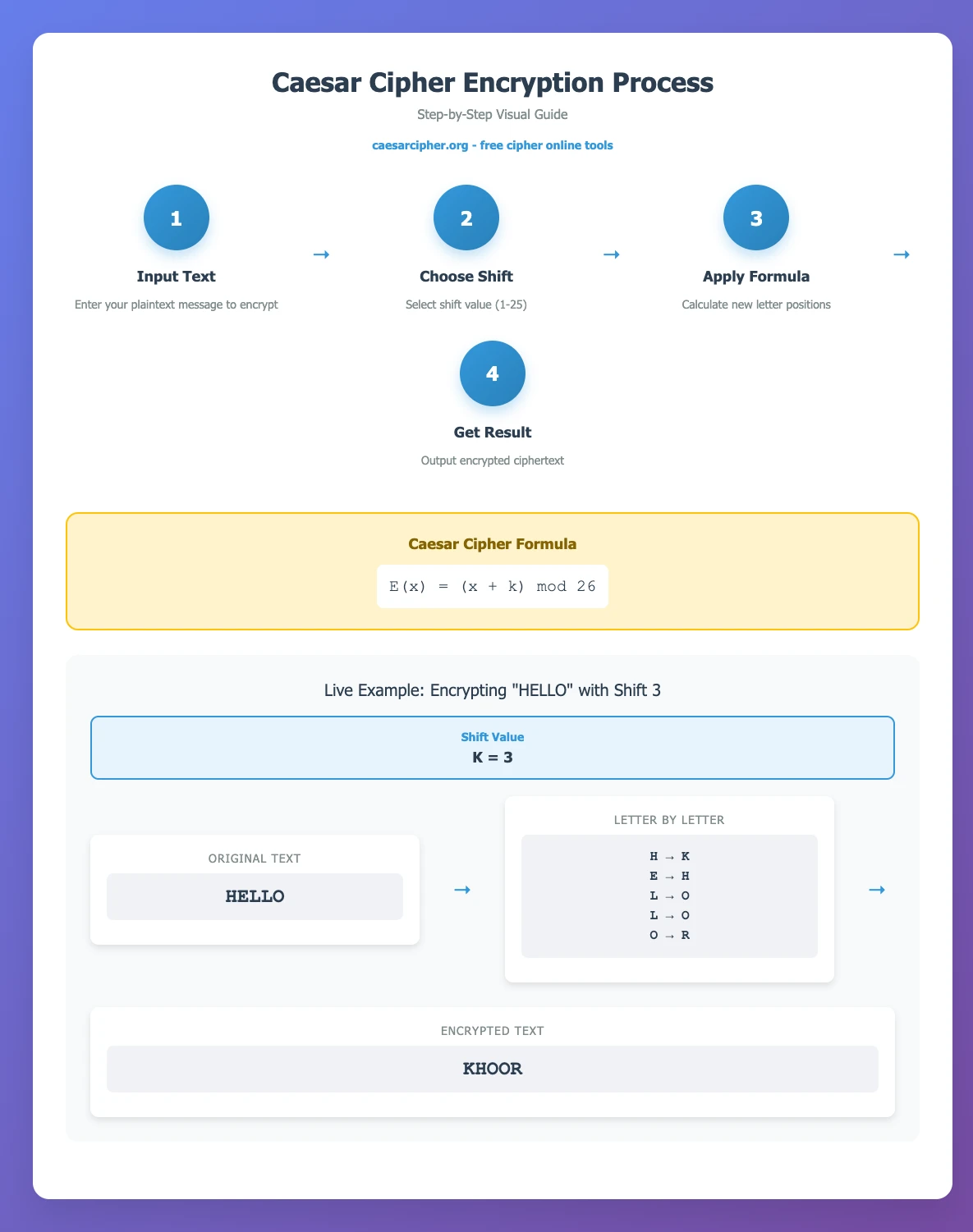
Mastering the Caesar cipher starts with understanding its basic encryption mechanism. Through manual calculations, we can deeply understand the principles of letter shifting and boundary handling techniques.
Exercise 1: Basic Encryption (Shift = 3)
Using the classic Caesar shift value of 3, encrypt the following sentence:
- Plaintext: "THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG"
- Encryption rule: Move each letter forward by 3 positions, with Z→A wraparound
Need a quick reference? Check our Caesar cipher alphabet table for easy letter mappings.
Solution Process:
Original alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Shifted alphabet: DEFGHIJKLMNOPQRSTUVWXYZABC
T → W, H → K, E → H
Q → T, U → X, I → L, C → F, K → N
Complete result: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD
Quick tip: I like to write out the shifted alphabet below the original when doing this by hand - it saves time and prevents errors. Trust me, after making this mistake in a timed competition once, I learned this lesson the hard way! Some people prefer counting on their fingers (no judgment!), but having the visual reference makes the whole process much smoother.
Exercise 2: Medium Shift Value (Shift = 7)
Encrypt the phrase: "MEET ME AT MIDNIGHT"
Solution: Using shift value 7: M→T, E→L, E→L, T→A... Result: "TLLA TL HA TPKUPNOA"
Exercise 3: ROT13 Challenge (Shift = 13)
ROT13 is a special case of the Caesar cipher. Since 13 is half of 26, encryption and decryption use the same operation, making it self-inverse.
Encrypt text: "HELLO WORLD PROGRAMMING"
Solution:
H → U, E → R, L → Y, L → Y, O → B
W → J, O → B, R → E, L → Y, D → Q
P → C, R → E, O → B, G → T, R → E, A → N, M → Z, M → Z, I → V, N → A, G → T
Result: "URYYB JBEYQ CEBTENZZVAT"
Pro Tip: ROT13 is widely used in online forums and newsgroups to obscure spoilers, offensive content, or puzzle solutions. Its self-inverse property makes it particularly convenient for quick encoding and decoding. Fun fact: if you've ever seen "spoiler alerts" on Reddit or old Usenet groups, there's a good chance someone used ROT13 to hide the punchline. It's like the internet's equivalent of "turn the page for the answer" in puzzle books!
Caesar Cipher Decryption Practice Problems
Decryption exercises develop your cryptanalysis skills and reverse-engineering thinking - crucial abilities for breaking unknown ciphers.
Decryption exercises cultivate reverse thinking abilities, which are core skills in cryptanalysis.
Challenge 1: Known Shift Value Decryption
Ciphertext: "DWWDFN DW GDZA", known shift = 3 Decryption steps: Move each letter backward by 3 positions
D → A, W → T, W → T, D → A, F → C, N → K
D → A, W → T
G → D, D → A, Z → W, A → X
Plaintext: "ATTACK AT DAWN"
Challenge 2: Unknown Shift Value Cracking
Ciphertext: "JHLZ PZ H ZLJYLA TLZZHNL"
Brute Force Method: Try all possible shift values (1-25), looking for meaningful English text. For systematic decoding techniques, see our complete decoder guide:
| Shift | Decryption Result | Evaluation |
|---|---|---|
| 1 | IGKY OY G YKJSKG SKYYGMK | ❌ Nonsensical |
| 2 | HFJX NX F XJIRJF RJXXFLJ | ❌ Nonsensical |
| 3 | GEIW MW E WIHQIE QIWWEKI | ❌ Nonsensical |
| 4 | FDHV LV D VHGPHD PHVVDJH | ❌ Nonsensical |
| 5 | ECGU KU C UGFORC OGUUCIG | ❌ Nonsensical |
| 6 | DBFT JT B TFENQB NFTTBHF | ❌ Nonsensical |
| 7 | THIS IS A SECRET MESSAGE | ✅ Meaningful! |
| 8 | SGHR HR Z RDBQDS LDRRZFD | ❌ Nonsensical |
Correct answer: shift = 7, plaintext: "THIS IS A SECRET MESSAGE"
Personal note: When I first learned this technique, I made the mistake of stopping at the first "reasonable-looking" result. Trust me, "SGHR HR Z RDBQDS LDRRZFD" might look like it could be some foreign language, but keep going! Your brain will know when you've found real English - it's unmistakable.
Advanced Caesar Cipher Character Handling
Real-world Caesar cipher implementations must handle mixed case text, numbers, punctuation, and special characters correctly.
Real-world text usually contains mixed case and punctuation marks, requiring more sophisticated handling strategies.
Exercise: Complex Text Encryption
Plaintext: "Hello, World! This is a test-123." Using shift = 5
Processing Rules:
- Uppercase letters: Shift within A-Z range
- Lowercase letters: Shift within a-z range
- Numbers and symbols: Remain unchanged
Solution Process:
H → M, e → j, l → q, l → q, o → t
W → B, o → t, r → w, l → q, d → i
T → Y, h → m, i → n, s → x
i → n, s → x
a → f
t → y, e → j, s → x, t → y
Result: "Mjqqt, Btwqi! Ymnx nx f yjxy-123."
Advanced Challenge: Preserving Word Boundaries
Try encrypting this sentence while maintaining readability: "The 2024 Olympics will feature 32 sports!"
With shift = 8:
- "The" becomes "Bpm"
- "Olympics" becomes "Wduuxtka"
- Numbers and punctuation stay the same
Final result: "Bpm 2024 Wduuxtka eodd pmibczm 32 axwzba!"
Want to practice with a physical tool? Learn how to make your own Caesar cipher wheel for offline practice.
Caesar Cipher Frequency Analysis and Cryptanalysis Techniques
Frequency analysis is the most powerful method for breaking Caesar ciphers without knowing the key. Learn professional cryptanalysis techniques used by security experts.
Frequency analysis is one of the most powerful tools for breaking Caesar ciphers. By analyzing letter occurrence frequencies, we can crack ciphertext without knowing the key.
Caesar Cipher Letter Frequency Analysis Methods
English letter frequencies provide the statistical foundation for breaking substitution ciphers through mathematical analysis.
English has clear letter frequency patterns: E (12.7%), T (9.1%), A (8.2%) are the most common letters, while Z (0.07%), Q (0.10%), X (0.15%) are least common.
Analysis Challenge: Long Ciphertext Breaking
Ciphertext (spaces removed): "WKLVLVDORQJHUGFUBSWRJUDSKLFPHVVDJHZLWKPDQBFKDUDFWHUVWKDWZLOOPKDNHIUHTXHQFBDQDOBVLVHDVLHU"
Frequency Analysis Steps:
- Count Letter Frequencies
L: 8 times, K: 7 times, V: 6 times, D: 6 times, U: 6 times
H: 5 times, W: 5 times, F: 4 times, Q: 4 times
-
Compare with English Letter Frequencies Highest frequency letter L likely corresponds to E Second highest K likely corresponds to T
-
Verify Hypothesis If L→E, shift value is: L(11) - E(4) = 7 If K→T, shift value is: K(10) - T(19) = -9 = 17 (equivalent to 7)
-
Test shift = 7
W → P, K → D, L → E, V → O
Ciphertext beginning "WKLV" decrypts to "THIS"
- Complete Decryption "THIS IS A LONGER CRYPTOGRAPHIC MESSAGE WITH MANY CHARACTERS THAT WILL MAKE FREQUENCY ANALYSIS EASIER"
Statistical Analysis Tips:
- For reliable frequency analysis, you need at least 100-200 characters
- Short texts may have skewed frequencies that mislead analysis
- Consider digraphs (TH, HE, IN) and trigraphs (THE, AND) for additional confirmation
- Use frequency analysis tools to verify your manual calculations
- Reference English letter frequency tables for accurate comparisons
From experience: I once spent an hour trying to crack a 50-character cipher using frequency analysis. The letter distribution was completely off because the message was "AARDVARK ZEBRA QUEEN JUMPED"! Short texts with unusual words can fool even experienced cryptanalysts. When frequency analysis fails, fall back to pattern recognition or good old brute force.
Caesar Cipher Pattern Recognition Techniques
Pattern recognition complements frequency analysis by identifying common English word structures and linguistic patterns in encrypted text.
Identifying common word patterns is another effective analysis method.
Three-Letter Word Patterns
Common three-letter words: THE, AND, FOR, ARE, BUT, etc.
Exercise: Pattern Recognition Breaking Ciphertext: "WKH TXLFN EURZQ IRA MXPSV RYHU WKH ODCB GRJ"
This is actually the famous pangram "The quick brown fox jumps over the lazy dog" - a sentence that contains every letter of the alphabet, making it perfect for cipher practice. You've probably seen this sentence when testing fonts or keyboards. Now you know why cryptographers love it too - it gives every letter a chance to appear, making frequency analysis more reliable.
Analysis Process:
- Identify "WKH" appearing twice → likely "THE"
- If W→T, then shift = 3
- Verify other words: TXLFN→QUICK, EURZQ→BROWN
- Confirm shift = 3 is correct
Decryption result: "THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG"
Advanced Pattern Recognition:
Single Letter Words: In English, only "A" and "I" appear as single letters
- If you see a single letter in ciphertext, it's likely "A" or "I"
Double Letter Patterns: Look for doubled letters like LL, SS, TT, EE
- In ciphertext "DWWDFN", the "WW" suggests doubled letters in plaintext
- Common doubles: ALL, EGG, BOOK, LOOK, etc.
Word Length Analysis:
- 2-letter words: TO, OF, IN, IT, IS, OR, AS, etc.
- 3-letter words: THE, AND, FOR, ARE, BUT, NOT, etc.
- Long words often contain common endings: -ING, -TION, -NESS
Caesar Cipher Brute Force Attack Methods
Brute force attacks systematically test all possible shift values - a guaranteed method for breaking any Caesar cipher.
When other methods fail, systematically trying all possible shift values remains the most reliable approach.
Complete Brute Force Demonstration
Ciphertext: "EXXEGOEXSRGI"
Complete attempt table:
| Shift | Candidate Plaintext | Evaluation |
|---|---|---|
| 0 | EXXEGOEXSRGI | ❌ Meaningless |
| 1 | DWWDFNDWRQFH | ❌ Meaningless |
| 2 | CVVCEMCVQPEG | ❌ Meaningless |
| 3 | BUUBDLBUPODF | ❌ Meaningless |
| 4 | ATTACKATONCE | ✅ Meaningful! |
| 5 | ZSSZBJZSNMBD | ❌ Meaningless |
| ... | ... | ... |
Efficiency Recognition Tips:
- Look for common word patterns (THE, AND, IS, etc.)
- Notice double letter combinations (LL, SS, TT, etc.)
- Check grammatical structure reasonableness
- Stop as soon as you find meaningful English text
Automated Brute Force Challenge: Write a simple program that tries all 25 shifts and ranks results by "English-ness" using:
- Vowel frequency (E, A, I, O, U should be ~40% of letters)
- Common word detection (THE, AND, TO, etc.)
- Absence of rare letter combinations (QX, ZJ, etc.)
- Try online tools like CyberChef to test your manual calculations
- Explore automated Caesar cipher solvers to verify your results
Caesar Cipher Programming Implementation Examples
Learn to implement Caesar cipher algorithms in JavaScript and Python with proper error handling, optimization techniques, and security considerations.
Programming implementations not only deepen understanding of algorithms but also handle large amounts of data and complex scenarios.
Basic Caesar Cipher Programming Examples
These fundamental implementations demonstrate proper Caesar cipher algorithm structure and common programming patterns.
Challenge 1: JavaScript Basic Implementation
Implement a caesarCipher function with requirements:
- Handle uppercase and lowercase letters
- Preserve non-alphabetic characters
- Support any shift value
Reference Solution:
Performance Optimization: For better performance with large texts, use ASCII math instead of indexOf:
Challenge 2: Python Enhanced Implementation
Implement a version supporting negative shift values and robust error handling:
Advanced Caesar Cipher Algorithm Development
Professional-grade implementations require automatic decryption, performance optimization, and robust error handling capabilities.
Automatic Decryption Implementation
Write a function that automatically detects the shift value and decrypts text. This is particularly useful for cryptanalysis challenges and CTF competitions:
Caesar Cipher CTF Competition Practice Problems
Capture The Flag (CTF) competitions often feature multi-layered Caesar cipher challenges that test advanced cryptanalysis skills.
Multi-Layer Encryption Challenge
Some CTF problems use multiple Caesar cipher rounds or combine them with other simple ciphers.
Challenge Scenario: A message was encrypted twice with Caesar cipher: first with shift=7, then shift=11. The final ciphertext is: "CZGG NZXR"
Solution Strategy:
- Two encryptions are equivalent to one shift=18 encryption
- Decryption requires shift=-18 → shift=8 (since -18 + 26 = 8)
Performance Optimization Challenge
For processing large files efficiently, consider these optimization techniques:
For real-world cryptography performance benchmarks, check out Crypto-JS benchmarks and performance comparisons. If you're looking for ready-made tools instead of coding your own, explore our collection of best free online Caesar cipher tools.
Caesar Cipher Learning Resources and Study Guide
Structured learning paths, recommended tools, and study strategies for mastering Caesar cipher techniques at your own pace.
Caesar Cipher Study Plans by Experience Level
Choose the learning path that matches your background and goals - from complete beginner to advanced cryptography student.
🌱 Scenario A: Complete Beginner Path
Week 1: Foundation Building
- ✅ Understand alphabet shifting principles
- ✅ Complete 5-10 manual encryption exercises
- ✅ Learn to use Caesar cipher wheels and online tools
- 🔊 Struggling with pronunciation? Check our audio guide on how to pronounce "Caesar cipher"
Week 2: Decryption Skills Training
- ⚙️ Practice brute force breaking methods
- 📈 Learn basic frequency analysis techniques
- 🛠️ Use online verification tools to check answers
Week 3: Pattern Recognition Enhancement
- 🧩 Identify common English word patterns (THE, AND, etc.)
- 📝 Practice analyzing different length ciphertexts
- 💻 Start simple programming implementations using Repl.it or CodePen
⚡ Scenario B: Fast Track for Programming-Experienced Learners
Days 1-3: Rapid Theory Mastery
- 📚 Read algorithm principles and mathematical representation
- 💻 Complete basic JavaScript/Python implementation
- 📉 Understand time complexity: O(n) encryption, O(26n) brute force
- 🎓 Study cryptography fundamentals on Coursera
Week 1: Advanced Implementation
- 🤖 Develop automatic decryption tools
- 📈 Implement frequency analysis algorithms
- 🌐 Create multi-language adaptations
- 📦 Explore Node.js crypto and Python cryptography libraries
Week 2: Competition Preparation
- 🏆 Solve HackerRank Caesar cipher problems
- 🛡️ Participate in picoCTF cryptography challenges
- ⚡ Optimize algorithm performance for large datasets
- 🔐 Join CryptoPals challenges for advanced practice
🏫 Scenario C: Teacher Guidance for Educational Implementation
⏰ 45-Minute Lesson Plan:
| Time | Activity | Resources |
|---|---|---|
| 0-5 min | 🎭 Historical Hook | Julius Caesar's cipher usage |
| 5-20 min | 📝 Theory & Demo | Interactive simulators |
| 20-40 min | 👥 Group Practice | Printable cipher wheels |
| 40-45 min | 💬 Wrap-up Discussion | Security implications & modern applications |
🎦 Teaching Resources:
- 📜 Download printable Caesar cipher wheel template
- 🎤 Use Kahoot quizzes for interactive assessment
- 📚 Assign Code.org cryptography lessons for homework
Assignment Design:
- Basic assignment: Complete 10 encryption exercises with different shift values
- Intermediate assignment: Program Caesar cipher encryption/decryption functions
- Challenge assignment: Analyze and crack given ciphertexts
- Use Kahoot quizzes for interactive assessment
- Assign Code.org cryptography lessons for structured learning
Best Caesar Cipher Learning Tools and Websites
Curated collection of the most effective online tools, practice platforms, and educational resources for Caesar cipher mastery.
Online Tool Platforms:
- CryptoClub.org - Interactive frequency analysis tools and educational materials
- dCode.fr - Comprehensive cryptography tool collection with Caesar cipher solver
- CyberChef - Multi-operation encoding and encryption toolkit from GCHQ
- Cryptii.com - Modern, user-friendly cipher tools with real-time processing
- Boxentriq - Advanced code-breaking tools with frequency analysis
Programming Practice Platforms:
- HackerRank - Caesar Cipher dedicated challenges with test cases
- LeetCode - Related string processing and algorithm problems
- picoCTF - Beginner-friendly cryptography competitions
- CryptoPals - Advanced cryptography challenges for serious learners
- CodeWars - Community-driven Caesar cipher coding challenges
Advanced Learning Resources:
- Khan Academy Cryptography - Basic cryptography course with interactive exercises
- Coursera Cryptography I - Stanford's comprehensive cryptography public course
- YouTube Cryptography Channels - Computerphile and other educational cryptography content
- MIT OpenCourseWare - Advanced computer security and cryptography
- Crypto101 - Free introductory course on cryptography principles
Caesar Cipher Common Errors and Debugging Tips
Avoid these frequent implementation mistakes and learn professional debugging techniques for Caesar cipher algorithms.
Implementation Pitfalls:
- Boundary Handling Errors
- Case Handling Confusion
- Non-Alphabetic Character Processing
- Off-by-One Errors in Manual Calculation
❌ Wrong: A=1, B=2, C=3... (1-indexed)
✅ Correct: A=0, B=1, C=2... (0-indexed)
💡 Remember: Computer science uses 0-based indexing!
Learning Misconceptions:
-
Over-reliance on Tools: Understanding principles is more important than using tools
- Solution: Always verify tool results with manual calculation first
- Resources: Practice with pen-and-paper exercises regularly
-
Ignoring Security Implications: Must understand why Caesar cipher is insecure in modern contexts
- Key insight: Only 25 possible keys makes brute force trivial
- Learn more: Read about modern cryptography standards from NIST
-
Lack of Practical Application: Theory without coding practice is insufficient
✅ Implementation Testing Checklist
Core Functionality Tests:
- Negative Shifts:
caesarCipher("ABC", -1)→"ZBC" - Case Preservation:
caesarCipher("Hello", 1)→"Ifmmp" - Non-Alphabetic:
caesarCipher("Hi!123", 1)→"Ij!123" - Empty String:
caesarCipher("", 5)→"" - Large Shifts:
caesarCipher("A", 29)→"D"(29 % 26 = 3) - Standard Test:
caesarCipher("THE QUICK BROWN FOX", 3)→"QEB NRFZH YOLTK CLU"
Edge Case Validation:
💡 Pro Tip: If you're like me and tend to overthink edge cases, start simple. Get the basic A-Z functionality working first, then add the bells and whistles. I've seen too many developers spend hours debugging complex case-handling logic when the core algorithm had a simple off-by-one error.
Frequently Asked Questions
How long does it take to solve Caesar cipher practice problems?
Beginners typically need 5-10 minutes for basic encryption/decryption problems and 15-30 minutes for frequency analysis challenges. With practice, experienced solvers can crack most Caesar ciphers in under 2 minutes.
Which Caesar cipher shift values are most commonly used?
Shift 3 (classic Caesar), shift 13 (ROT13), and shifts 1, 5, 7 are most popular. In CTF competitions, organizers often use less obvious shifts like 11, 17, or 23 to prevent quick guessing.
What's the best way to practice Caesar cipher frequency analysis?
Start with longer texts (200+ characters) for reliable frequency patterns. Practice with real English passages rather than artificial text. Use frequency analysis tools to verify your manual calculations.
Can I use Caesar cipher for real security purposes?
No! Caesar cipher provides no real security - it can be broken in seconds. It's purely educational. For actual security, use modern encryption like AES-256 or RSA.
What programming language is best for Caesar cipher implementation?
JavaScript and Python are excellent for beginners due to simple syntax. C++ and Java offer better performance for large texts. Choose based on your current skills and learning goals.
Caesar Cipher Mastery Summary and Next Steps
Congratulations! You've completed a comprehensive Caesar cipher training program covering encryption, decryption, frequency analysis, and programming implementation.
Through the systematic practice in this article, you should have mastered the core skills of Caesar cipher:
Caesar Cipher Skills Mastered:
- ✅ Manual Encryption/Decryption: Quick letter shifting calculations and cipher verification techniques
- ✅ Cryptanalysis Methods: Frequency analysis, pattern recognition, and systematic brute force attack methods
- ✅ Programming Expertise: Caesar cipher algorithm implementation and optimization in JavaScript and Python
- ✅ Cryptographic Thinking: Systematic cipher analysis methodology and security evaluation skills
Practical Value Demonstration: These skills apply not only to Caesar cipher, but also lay the foundation for learning more complex cryptographic algorithms. Frequency analysis techniques can be applied to other monoalphabetic substitution ciphers, and programming implementation experience can extend to Vigenère cipher, RSA algorithm, and other modern encryption methods.
Real-World Applications:
- Cybersecurity Competitions: Your skills directly apply to CTF events worldwide
- Educational Technology: Create interactive learning tools for teaching cryptography
- Historical Research: Decrypt historical documents and ciphers
- Software Development: Build secure communication tools with proper encryption
- Tool Development: Use your knowledge to evaluate and improve existing Caesar cipher tools or build better ones
Next Learning Directions:
- Advanced Substitution Ciphers: Learn simple substitution cipher and affine cipher
- Polyalphabetic Cipher Exploration: Deep dive into Vigenère cipher and Playfair cipher
- Modern Cryptography Introduction: Understand symmetric encryption and public key cryptosystems
- CTF Competition Participation: Apply theoretical knowledge to actual security challenges on CTFtime and OverTheWire
Extended Learning Path:
- Week 4-6: Master Vigenère cipher breaking techniques
- Month 2-3: Study RSA cryptography fundamentals
- Month 4-6: Explore elliptic curve cryptography and modern standards
- Ongoing: Participate in security conferences and cryptography meetups
Remember, cryptography is a highly practical discipline. Understanding theory alone is insufficient - continuous practice and challenges are what truly improve your skill level. Whether for academic research, professional needs, or pure interest, maintain curiosity and hands-on practice habits. You'll discover more excitement in the world of cryptography.
Think of it like learning to drive - you can memorize every traffic rule in the book, but until you're actually behind the wheel navigating real traffic, you're not truly a driver. Cryptography is the same way. Every cipher you crack, every algorithm you implement, every CTF challenge you solve makes you more comfortable with the patterns and thinking required for real cryptographic work.
Ready for Advanced Cryptography Challenges?
Now that you've mastered Caesar cipher techniques, you're prepared to tackle more sophisticated encryption algorithms and cryptanalysis challenges. Choose your next cryptographic adventure:
- Advanced Substitution Ciphers: Master Vigenère cipher, Playfair cipher, and polyalphabetic encryption methods
- Programming Challenges: Build advanced cryptanalysis tools, contribute to open-source security projects, and develop cipher-breaking algorithms
- Historical Cryptography: Apply your skills to decrypt authentic historical messages, wartime communications, and classical cipher texts
- Cybersecurity Competition: Join CTF competitions, solve cryptography challenges, and test your skills against other security enthusiasts
- Modern Cryptography: Study RSA encryption, elliptic curve cryptography, and contemporary security protocols
The beautiful thing about cryptography is that every expert started exactly where you are now - with curiosity and a willingness to tackle that first "impossible" looking cipher. You've got this!
Recommended Next Steps:
- Try the NSA's Cryptanalysis courses
- Join the Cryptography Stack Exchange community
- Follow modern cryptography research developments
- Build your own cryptographic portfolio on GitHub